While most CRM administrators understand that aspect, there are a number of settings and configurations that lead up to this issue that are less well-known to most. One of the biggest complexities is understanding EXACTLY when CRM will be going down because of the Auto Certificate Rollover and how to avoid it. We will be going through that today.
We will start with the process that ADFS goes through for certificate renewal:
- ADFS determines that its certificates will be expiring soon.
- ADFS creates new certificates and sets them as secondary certificates.
- ADFS updates the new certificates to primary certificates.
There are a number of settings for ADFS only accessible via PowerShell that control the Auto Certificate Rollover options and properties for the process above. To access these, open an administrative PowerShell prompt and execute the following (Note that if you are using ADFS 2.0, you will need to add the ADFS PowerShell Snap-In first by executing Add-PSSnapin Microsoft.ADFS.PowerShell):
 Get-ADFSProperties
Get-ADFSProperties- AutoCertificateRollover
- CertificateDuration
- CertificateGenerationThreshold
- CertificatePromotionThreshold
- CertificateRolloverInterval
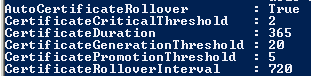
So what do all of these values mean? Below are the same steps provided earlier but now account for the values in the table above.
- ADFS determines that its certificates will be expiring within 20 days.
- ADFS creates new certificates valid for 365 days and sets them as secondary certificates.
- After 5 days’ time the Certificate Management Cycle kicks off and ADFS updates the new certificates to primary certificates.
As you can see, knowing these values can greatly help in planning for certificate rollover. Here is an example:
In the screenshot below, we can see our primary certificates expire on 2/12/2015 and ADFS has already created new certificates to rollover. The new (secondary) certificates were created 20 days prior to the expiration of the primary certificates (1/23/2015). On 1/28/2015, 5 days after the creation of the new certificates, ADFS will change them to primaries.
Great. So what now? BEAT ADFS TO THE PUNCH!
In the above example, you know your deadline is 1/28/2015. Rather than sitting back and waiting until CRM goes down, plan a short outage afterhours and roll the certificates over manually! You can force ADFS to generate new certificates and promote them to primaries immediately using the following command in PowerShell:
Once the new certificates are in place in ADFS, re-run the Claims and IFD Wizards in the CRM Deployment Manager to update the metadata and issue an IISReset on the CRM server(s). Voila! Happy CRM users!
Of course, given the properties we have at our disposal to modify there is much more you can do to create a better life for yourself. For example, set the CertificateDuration to 1095 days (three years) rather than just 365 (one year) so this is not as frequent of an issue. Another idea would be to set the CertificateGenerationThreshold lower so the actual rollover date is closer to the true expiration of the certificate. Or just turn off AutoCertificateRollover altogether, set a reminder, and take care of it all manually before expiration!


No comments:
Post a Comment